
Microsoft Entra ID Security Defaults: Your First Line of Defence
Microsoft Entra ID Security Defaults
Microsoft Entra ID’s security defaults provide an essential layer of protection against identity-related attacks, such as password spraying and man-in-the-middle attacks. In this article, we’ll delve into the five pre-configured security policies, their benefits, and how to enable them.
What are Security Defaults?
Security defaults are a set of pre-configured security policies designed to enhance your organisation’s security posture. These policies are enabled by default for tenants created after October 2019 and are available at no extra cost.
Five Pre-Configured Security Policies
- Require all users to register for Microsoft Entra MFA
- Require administrators to use MFA
- Require users to use MFA when necessary
- Block legacy authentication protocols
- Protect privileged activities
Who Should Use Security Defaults?
Organisations using the free tier of Microsoft Entra ID licensing and those seeking to enhance their security posture without complex configurations.
Enabling Security Defaults
- Navigate to
Identity > Overviewin the Microsoft Entra ID portal - Click on Properties
- Manage security defaults
- Enable security defaults
Best Practices and Recommendations
- Organisations with Microsoft Entra P1 and P2 licenses should consider using conditional access policies for more complex security requirements.
- Security defaults are suitable for organisations without existing conditional access policies.
- MFA significantly mitigates identity threats; enable security defaults or conditional access policies to ensure robust protection.
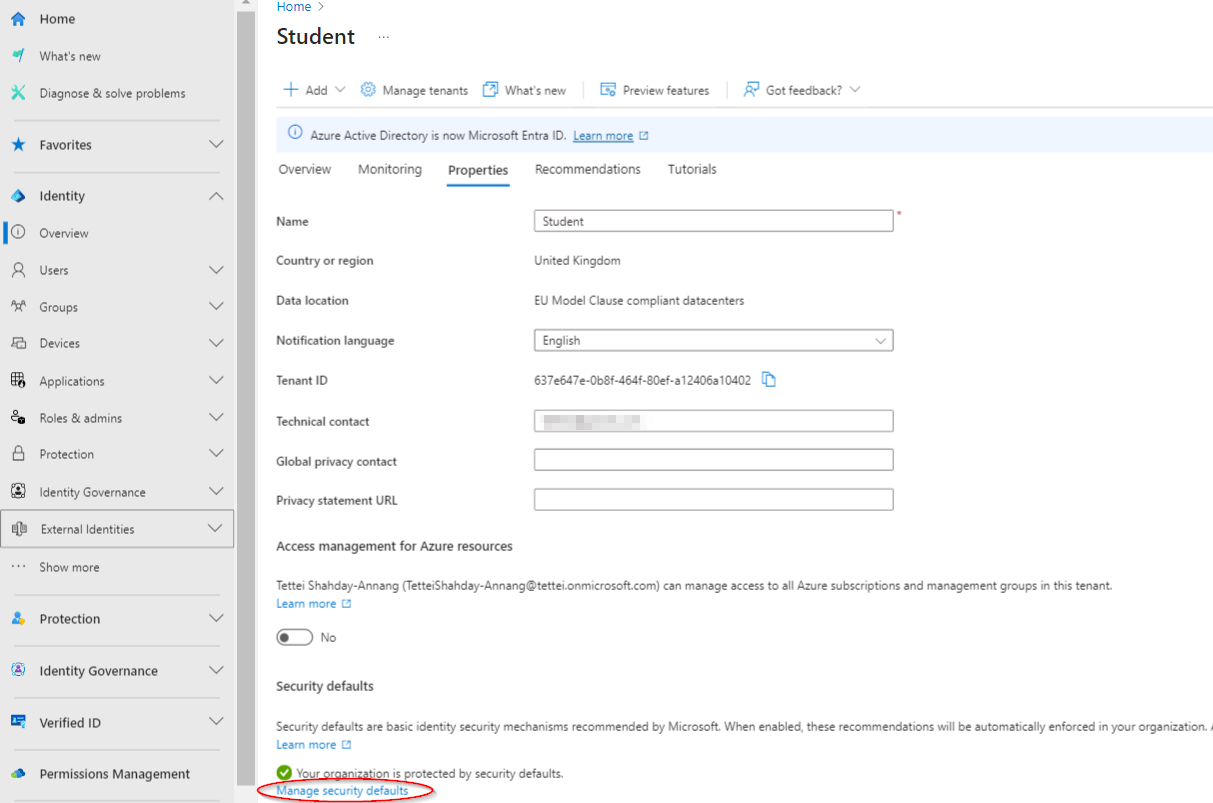 Enabling security defaults in Microsoft Entra ID
Enabling security defaults in Microsoft Entra ID
By understanding and enabling security defaults, you’ll significantly enhance your organisation’s security posture and protect against identity-related attacks.