
Understanding Identity and Access Management (IAM) with Microsoft Entra ID
Microsoft Entra ID IAM
Identity Fundamentals
In identity solutions, three key concepts are crucial: identity, authentication, and authorization.
- Identity: A digital identity is a collection of unique identifiers or attributes representing an individual, software component, device, or entity in a computer system. There are three types: human identities, workload identities, and device identities.
- Authentication: The process of verifying a person, software component, or hardware device’s credentials to confirm their identity.
- Authorization: Validates user access to resources, detailing what actions they can perform.
Identity Providers
An Identity Provider (IdP) manages identity information, offering authentication, authorization, and auditing services. A central IdP simplifies and secures user identity management.
Some prominent identity providers include:
- Microsoft Entra ID
- Social media platforms like X, Google, Facebook, and LinkedIn
- Cloud services like Amazon
- Development platforms like GitHub
- Specialized identity management solutions like Okta
These providers offer distinct features and capabilities, catering to their respective ecosystems. However, they all share a common objective: to deliver secure, reliable, and efficient identity management and authentication services, ensuring seamless and protected access to resources.
What is Identity and Access Management (IAM)?
IAM is a framework ensuring the right people have appropriate access to technology resources. IAM systems manage user identities and access rights across various systems and applications.
- Identity Management: Creation, storage, and management of user identities.
- Identity Federation: Allows users with existing credentials to access systems without separate login credentials.
- Provisioning and Deprovisioning: Setting up and managing user accounts, specifying access to resources and assigning permissions.
- Authentication: Verifying user identity.
- Authorization: Ensuring appropriate access to resources based on user entitlements.
- Access Control: Defining and enforcing policies regulating access to resources.
- Reports and Monitoring: Generating reports on actions taken within the platform.
How IAM Works
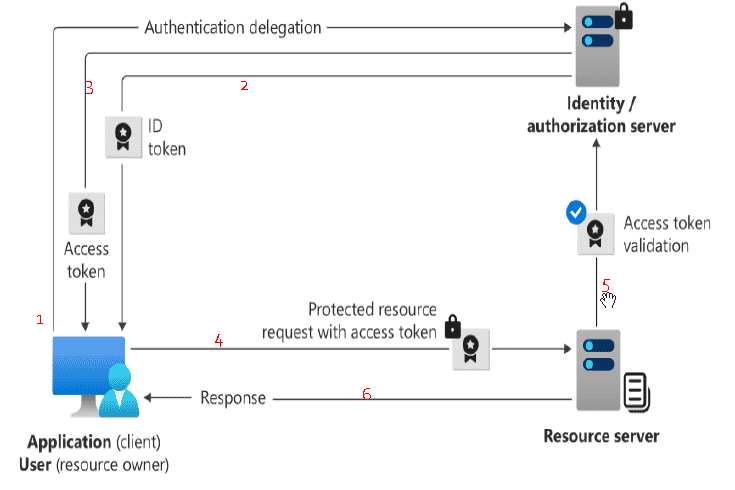
-
The user (resource owner) initiates an authentication request to the identity provider/authorisation server from the client application.
-
Upon verifying the credentials, the identity provider/authorisation server sends an ID token containing user information back to the application.
-
The identity provider/authorisation server obtains end-user consent and grants authorisation to the client application to access the protected resource, issuing an access token.
-
The client application attaches the access token to subsequent requests made to the protected resource server.
-
The identity provider/authorisation server validates the access token, and if successful, grants access to the protected resources, sending a response back to the client application.
In conclusion, Identity and Access Management (IAM) is a critical component of modern security infrastructure, ensuring that the right individuals have appropriate access to technology resources. Microsoft Entra ID offers a robust IAM solution, streamlining identity management, authentication, and authorization processes. By understanding the fundamentals of IAM and how Microsoft Entra ID works, organizations can enhance security, improve operational efficiency, and reduce the risk of unauthorized access. As technology continues to evolve, IAM will remain a vital aspect of protecting sensitive data and resources.