In Google’s Cybersecurity Professional course, I actively contributed to a critical project within the research team at my organization. The primary goal was to enhance the security of our system by updating file permissions for specific files and directories within the projects directory. The existing permissions did not align with the desired level of authorization, posing potential security risks. My responsibilities included:
Table of contents
Open Table of contents
Analyzing File and Directory Permissions
The code below illustrates how I used Linux commands to check the current permissions for a specific directory in the file system.
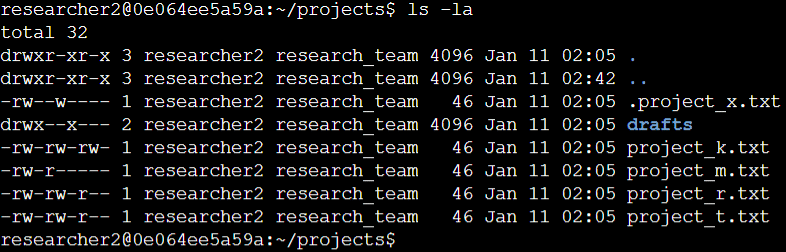
The initial line in the screenshot shows the command I entered, while the subsequent lines present the output. The code provides a listing of all items in the projects directory. I employed the ls command with the -la option to exhibit a detailed list of file contents, including hidden files. The output reveals key information: one directory called drafts, a concealed file labeled .project_x.txt, and five other project files. The 10-character string in the first column denotes the permissions for each file or directory.
Describing the Permissions String
The 10-character string can be broken down to identify who has permission to access the file and the specific permissions granted. Here’s a breakdown of the characters and their meanings:
-
1st character: This character is either a
dor a hyphen (-), indicating the file type. If it’s ad, it’s a directory; if it’s a hyphen (-), it’s a regular file. -
2nd-4th characters: These characters signify the read (
r), write (w), and execute (x) permissions for the user. A hyphen (-) in any of these positions indicates the absence of that permission for the user. -
5th-7th characters: These characters represent the read (r), write (
w), and execute (x) permissions for the group. A hyphen (-) in any of these positions means the absence of that permission for the group. -
8th-10th characters: These characters denote the read (
r), write (w), and execute (x) permissions for others. This category includes all users on the system except the user and the group. A hyphen (-) in any of these positions signifies the absence of that permission for others.
For instance, consider the file permissions for project_t.txt, which are -rw-rw-r--. The initial hyphen (-) indicates that project_t.txt is a file, not a directory. The second, fifth, and eighth characters are r, indicating that the user, group, and others all have read permissions. The third and sixth characters are w, indicating that only the user and the group have write permissions. There are no execute permissions for project_t.txt.
Changing File Permissions
Upon the organization’s decision to restrict write access for other users to all files, I referred to the previously obtained file permissions. Specifically, I identified that project_k.txt needed to have write access removed for other.
The following code showcases how I executed Linux commands to achieve this:
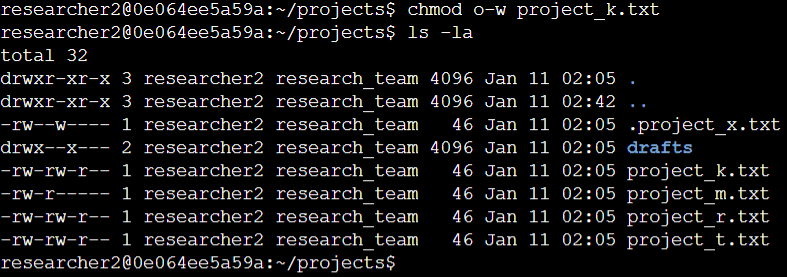
The first two lines in the screenshot display the commands I entered, while the subsequent lines present the output of the second command. Leveraging the chmod command, which is used to modify permissions on files and directories, I specified other as the target. The first argument indicated the permissions to be changed, and the second argument specified the file (project_k.txt).
For clarification, I removed write permissions from other for the project_k.txt file. To confirm the changes made, I utilized ls -la to review the updated permissions.
Changing Permissions on a Hidden File
The research team at my organization recently archived project_x.txt. They aim to restrict write access to this project, allowing only the user and group to have read access. The following code outlines how I utilized Linux commands to modify the permissions:
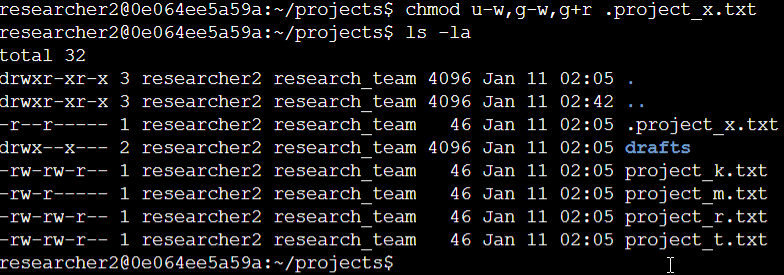
The initial two lines in the screenshot present the commands I entered, and the subsequent lines illustrate the output of the second command. Recognizing that .project_x.txt is a hidden file due to its period prefix, I executed specific commands in this example. I revoked write permissions from both the user and group using u-w and g-w, respectively. Additionally, I granted read permissions to the group with g+r.
Enhancing Directory Access Control
In alignment with organizational policies, exclusive access to the drafts directory and its contents is designated for the researcher2 user. Consequently, no one else but researcher2 should possess execute permissions.
The following code exemplifies how I employed Linux commands to modify these permissions:
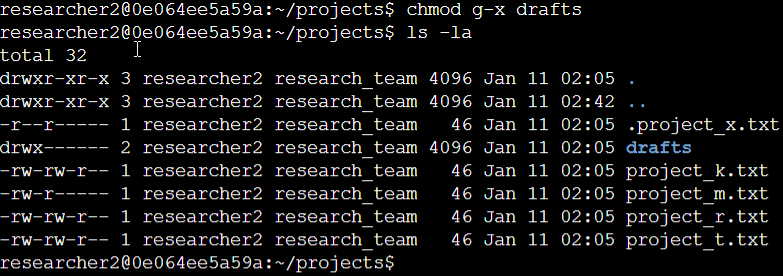
The initial two lines in the screenshot showcase the commands I entered, and the subsequent lines present the output of the second command. Having previously identified that the group held execute permissions, I utilized the chmod command to eliminate them. Given that researcher2 already had execute permissions, no further adjustments were necessary.
Project Summary
In summary, my contributions resulted in a comprehensive alignment of file and directory permissions with the organization’s security requirements. The initial assessment using ls -la provided essential insights, guiding subsequent decisions. Leveraging the chmod command, I systematically adjusted permissions, ensuring a robust security posture for our projects directory. This project showcased my proficiency in Linux commands and my ability to proactively address cybersecurity concerns through effective permission management.